Sum-up
TL;DR
Target is Hosting a NibbleBlog CMS. Version is vulnerable to CVE-2015-6967 but requires valid login credentials.
Enumeration leads to accessing CMS files, containing a
user.xmlshowing admin. Guessing password (nibbles) allow for authentication. Note that Blacklisting protection is active to avoid bruteforce. The CVE vulnerability can be exploited to gain a shell on the server.A
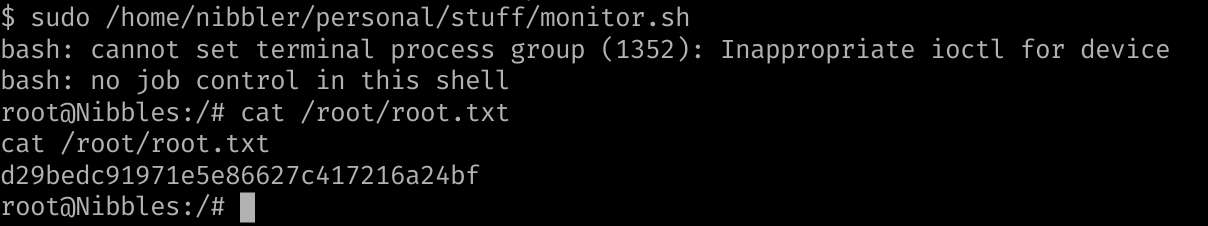
monitor.shscript on nibbler folder has SETUID bit and allow for root privilege escalation.
Vulnerabilities
- Broken Access Control
- Sensitive Data Exposure
- file upload
- Remote Code Execution
- Local Privilege Escalation
Flags
user.txt
9e105d81eef0b735c618fd48ed3a73f9
root.txt
d29bedc91971e5e86627c417216a24bf
Write-up
Enumerate host, services
3 different nmap scan :
nmap $ipscopenmap $ipscope -p- -Pnnmap $ipscope -sU
Work with first nmap scan results while the 2 remaining are running :
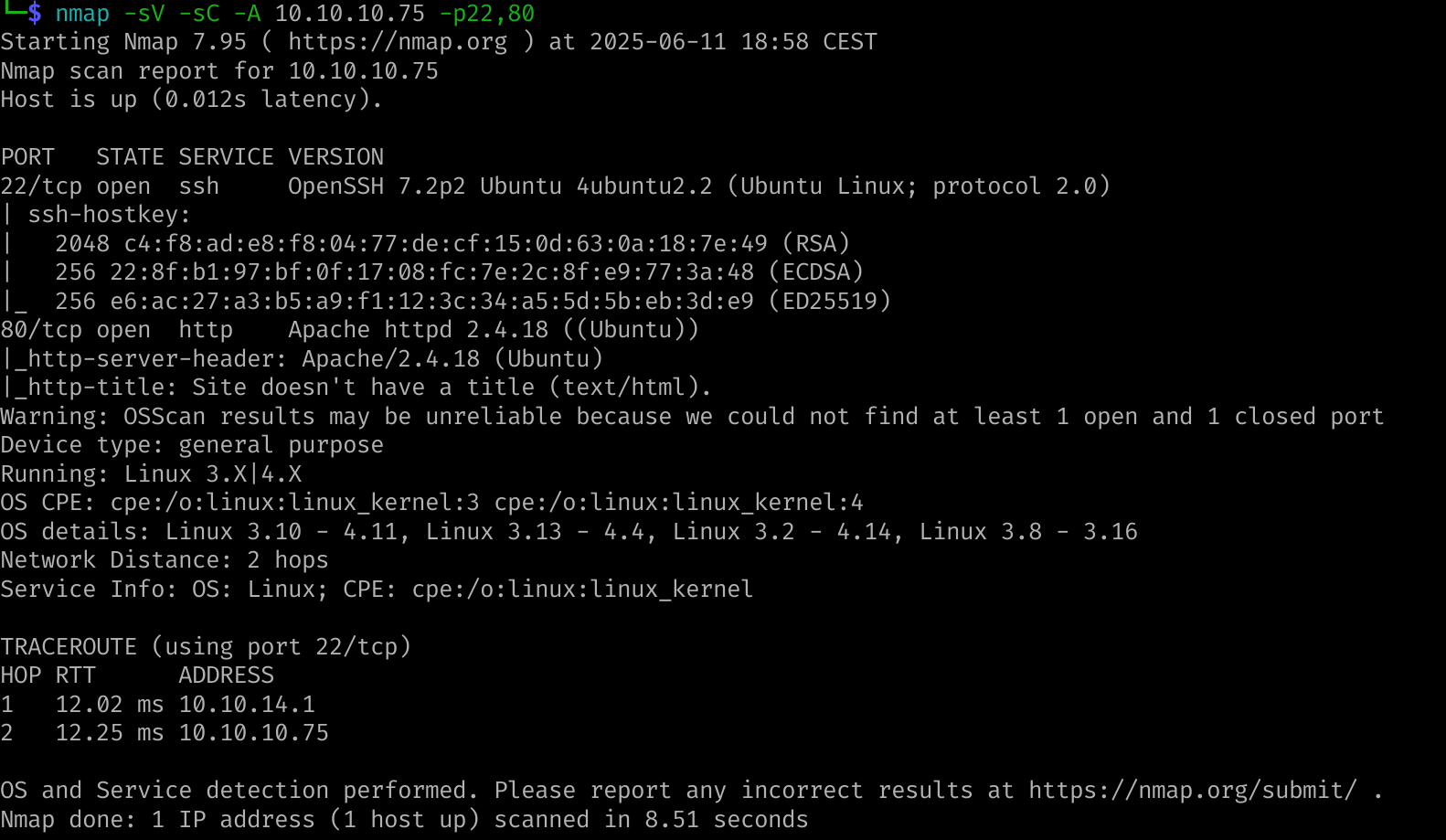
Enumerate versions on found services :
Host and services :
SSH server Apache 2.4.18 HTTP server Linux 3.X |4.X
Starting Apache server enumeration first.
Apache Server
Reaching IP on browser returns a Hello World blank page, inspect content :

Lookup Nibble
From now on we have many checks to do.
- Search for nibbleblog server, CVE, version etc…
- Enumerate directories and files
- Check pages source code same as we did on root page.
Enumerate vhosts
We can and enumerate on vhosts and file directory from /nibbleblog/ :

No vhost
Apparently no vhosts are set up on the server which limits the scope to work with
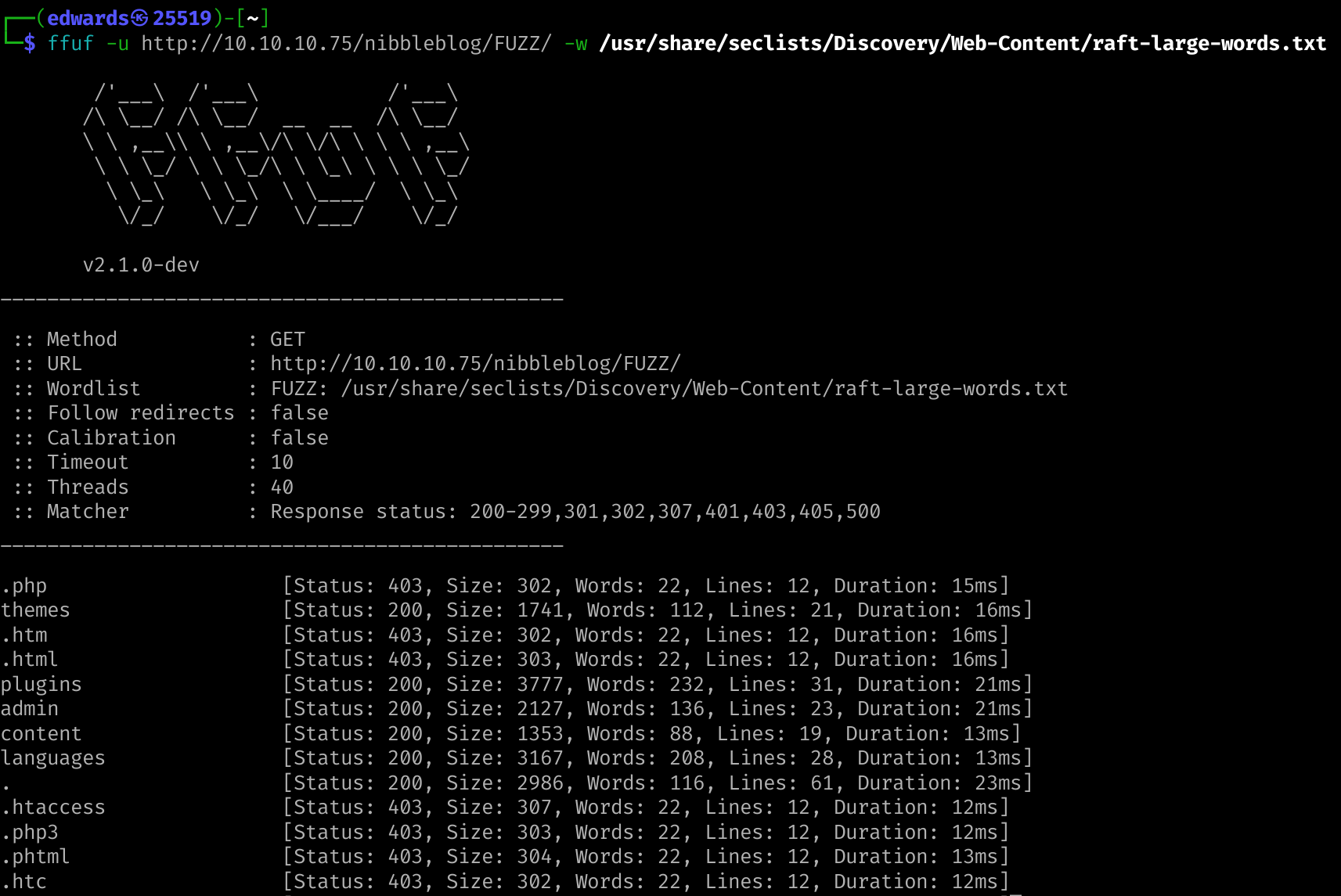
Enumerate directories and files
Start the enumeration and in the meanwhile lookup for Nibbleblog :
Public Exploits
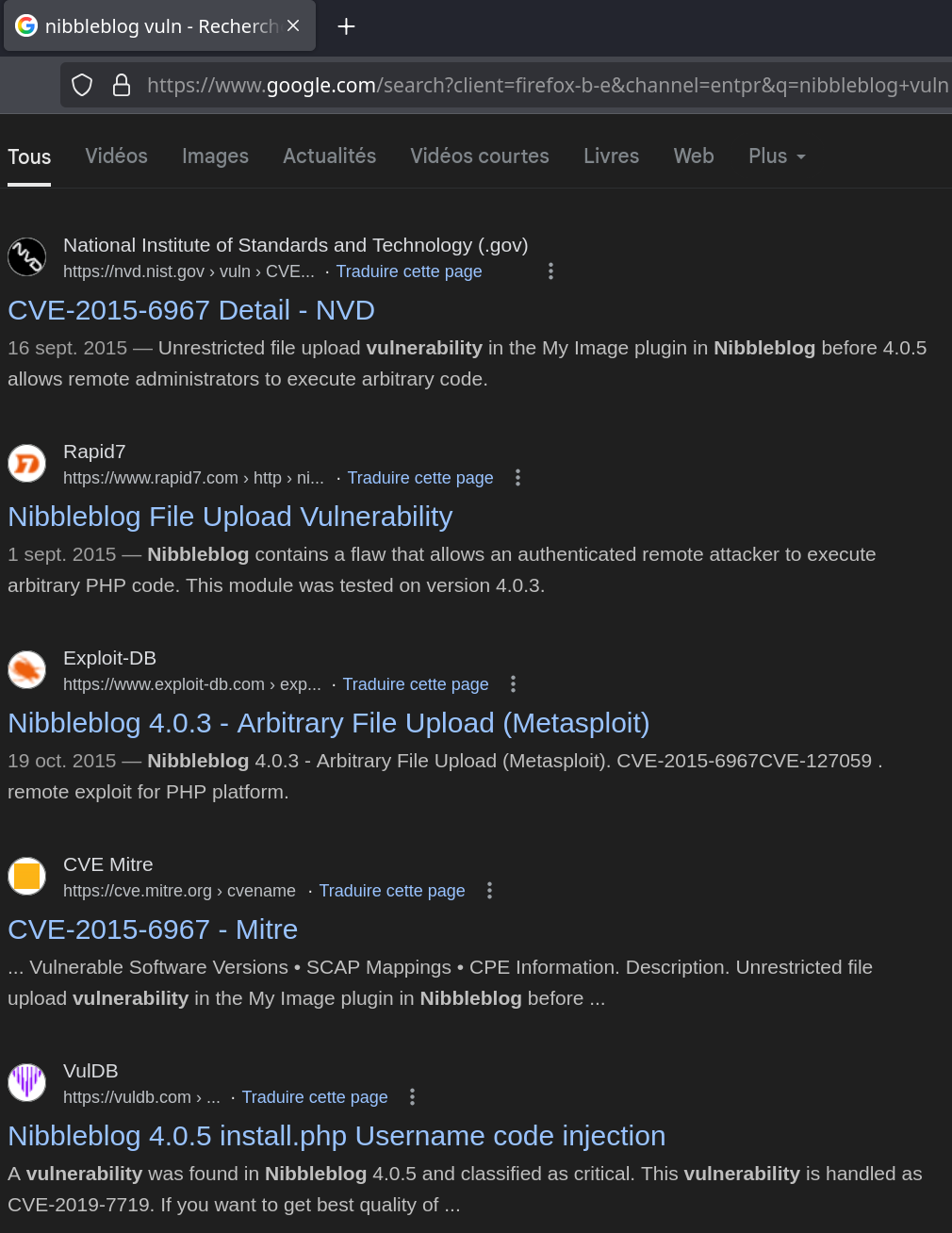
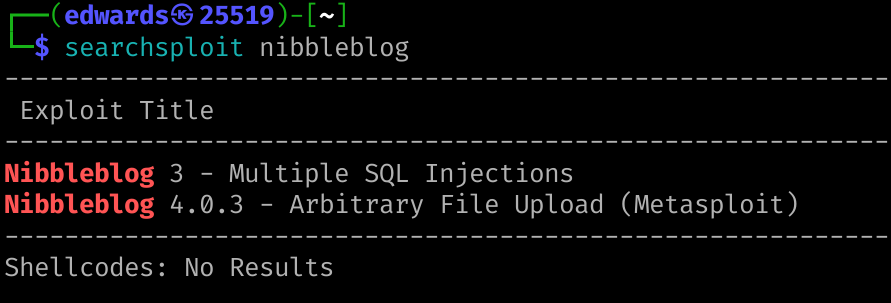
The file Upload requires authentication, which means we can login to the server.
Exploiting enumeration results
Enumerate directories and files gave us a 200 on /nibbleblog/admin/ :
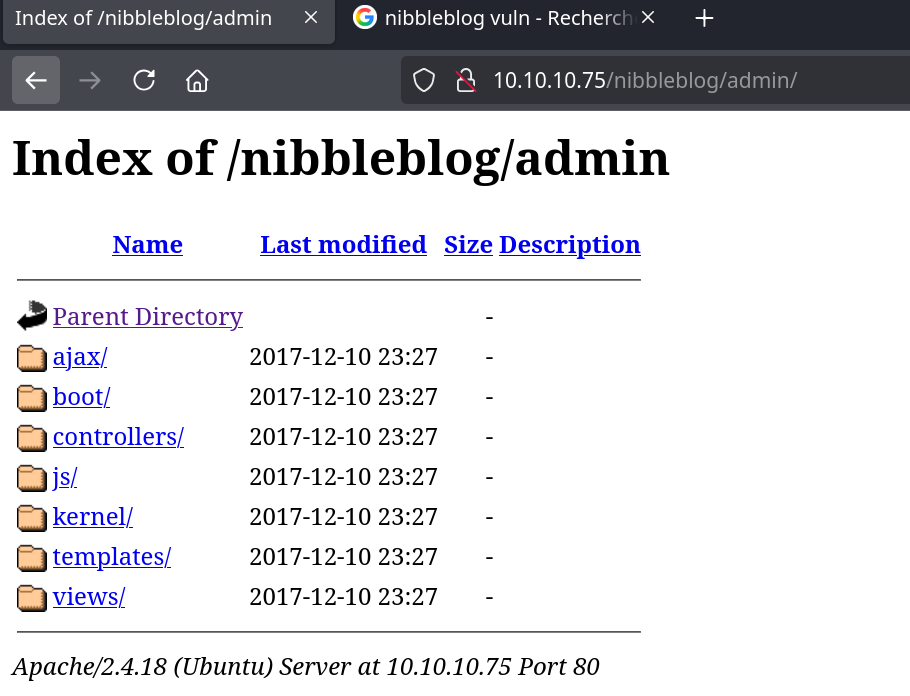
We have a first vulnerability for Broken Access Control and Sensitive Data Exposure. We can dig through each path using the content discovery from Burpsuite to get a good site-map of the application.
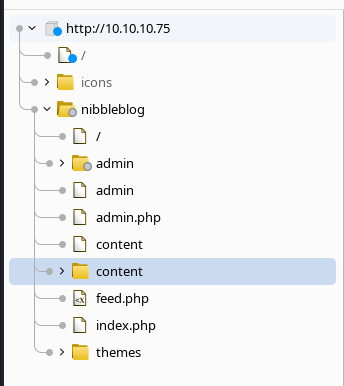
Exploring the application and reaching /nibbleblog/content/private/users.xml gives us :
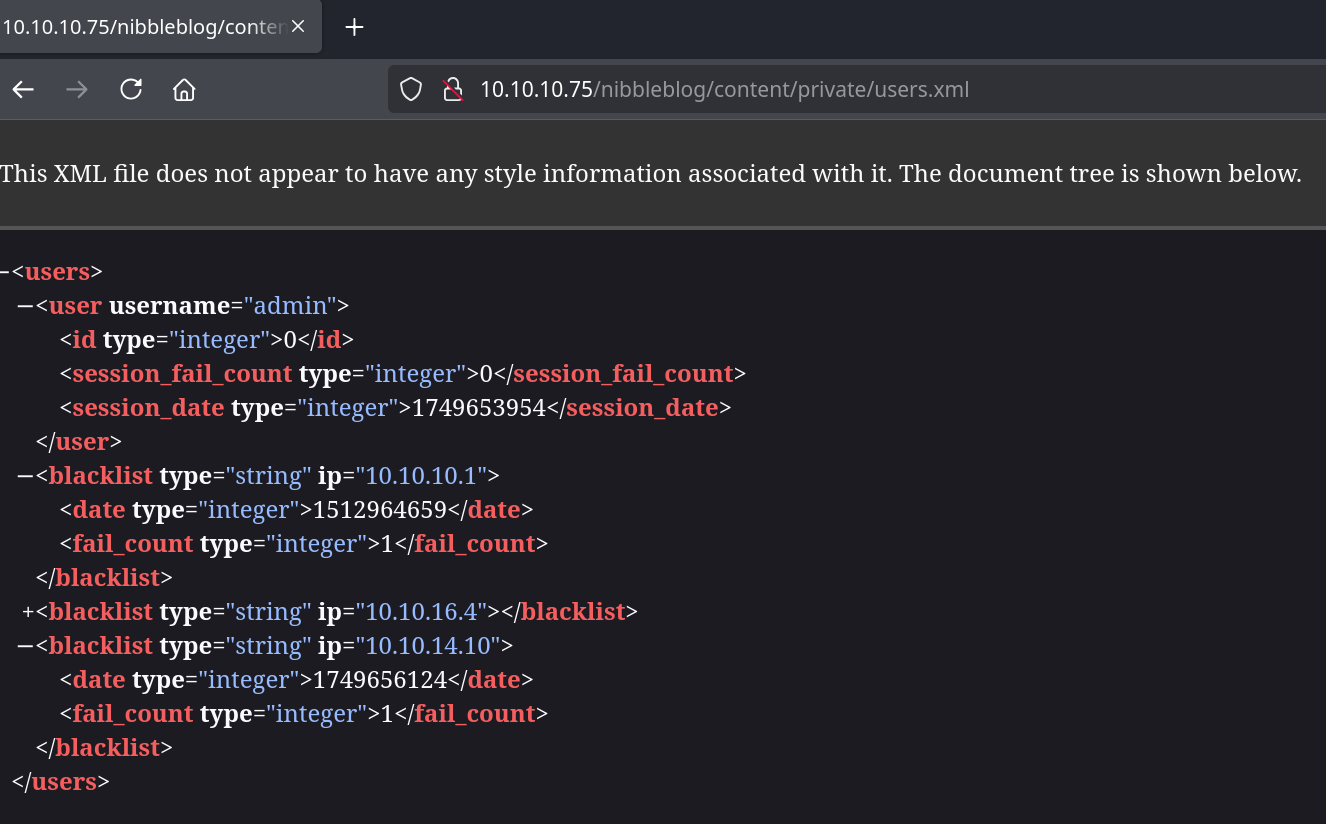
admin seems to exists as a user. By reaching admin.php from enumeration we get on a login portal :
By trying too many login connection, we end up on a server response indicating Blacklist protection. +1 for the client we cannot bruteforce login.
admin:admin is invalid.
admin:nibbles let us authenticate.
Remember Public Exploits
We had file upload Vulnerabilities from our research on Nibbles. We’re authenticated and we can try to exploit it.
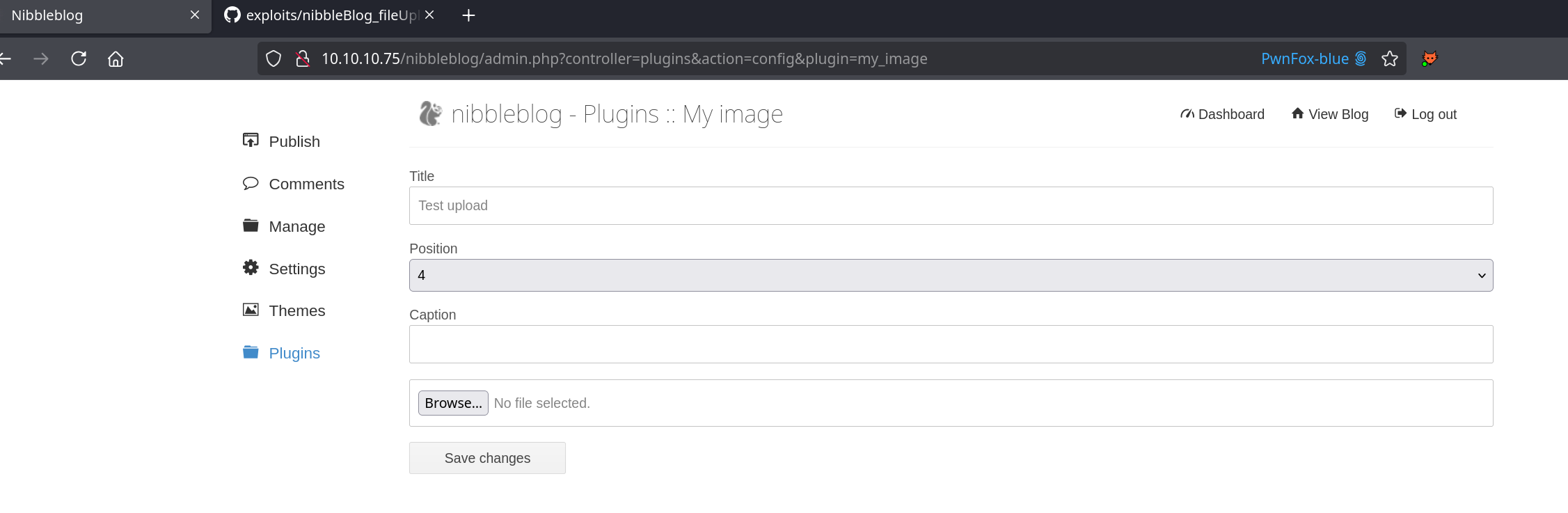
Use pentest-monkey php-reverse-shell.php as the picture. No filtering is done server side and our payload is available at /nibbleblog/content/private/plugins/my_image/image.php
We now have a file upload vulnerability that leads to Remote Code Execution.
Setting up a listener and reaching the path gets us a reverse shell. We could add a SSH-key since the SSH server is enabled here.
Metasploit options
You can also use metasploit for the CVE-2015-6967.
user.txt ; escalating to root
We are connected as nibbler on the machine :
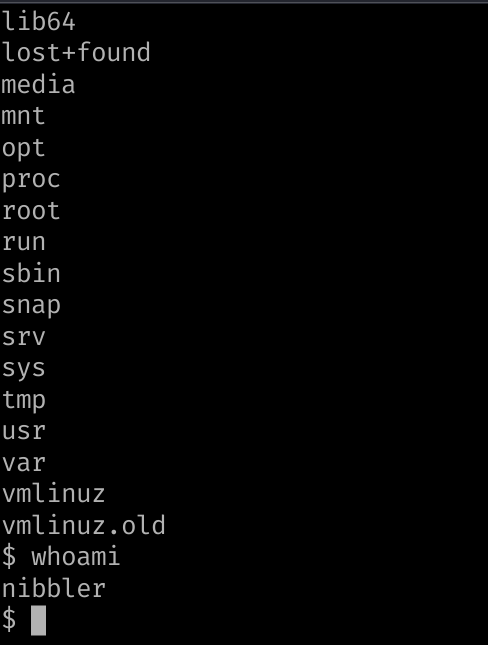
We can deploy enumeration scripts or already submit a sudo -l which returns :
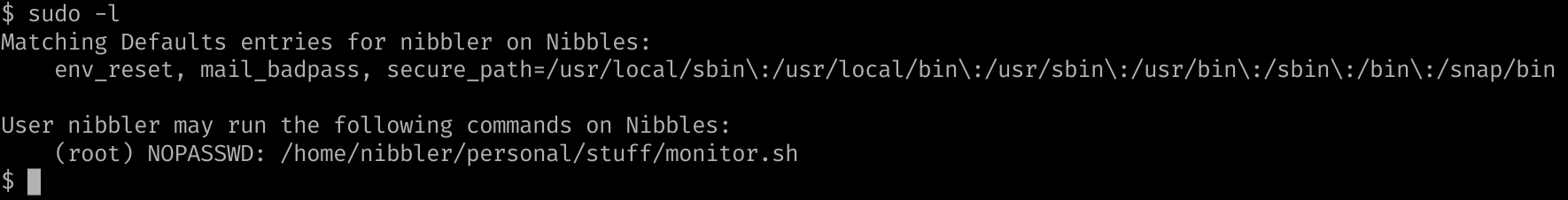
We can then sudo /home/nibbler/personal/stuff/monitor.sh to gain root level access to the machine :